In this two part series, we explore the concerning and escalating timeline of modern ransomware attacks
The cost of ransomware in 2023 is almost 57 times more than it cost in 2015 with the current price tag sitting at $20 billion. This voracious attack vector has seen a 30% growth year-on-year but was at its most vicious in 2016 and 2021 – two years that saw ransomware exceed 600 million attacks, according to Statista. Since 2015, there has also been a sharp increase in the volume of ransomware families with only 29 in 2015 all the way through to 327 in 2017 and 78 in 2021 – these numbers may hint at waves of attack, but when looked at through the lens of organisations victimised by the malware, it has seen a steady increase from 55% in 2018 to 71% in 2022.
It is gaining ground.
This trend can be seen in the type and volume of large attacks over the past eight years. In this two-part series, we dig into the threats and build a timeline that’s not for the faint-hearted…
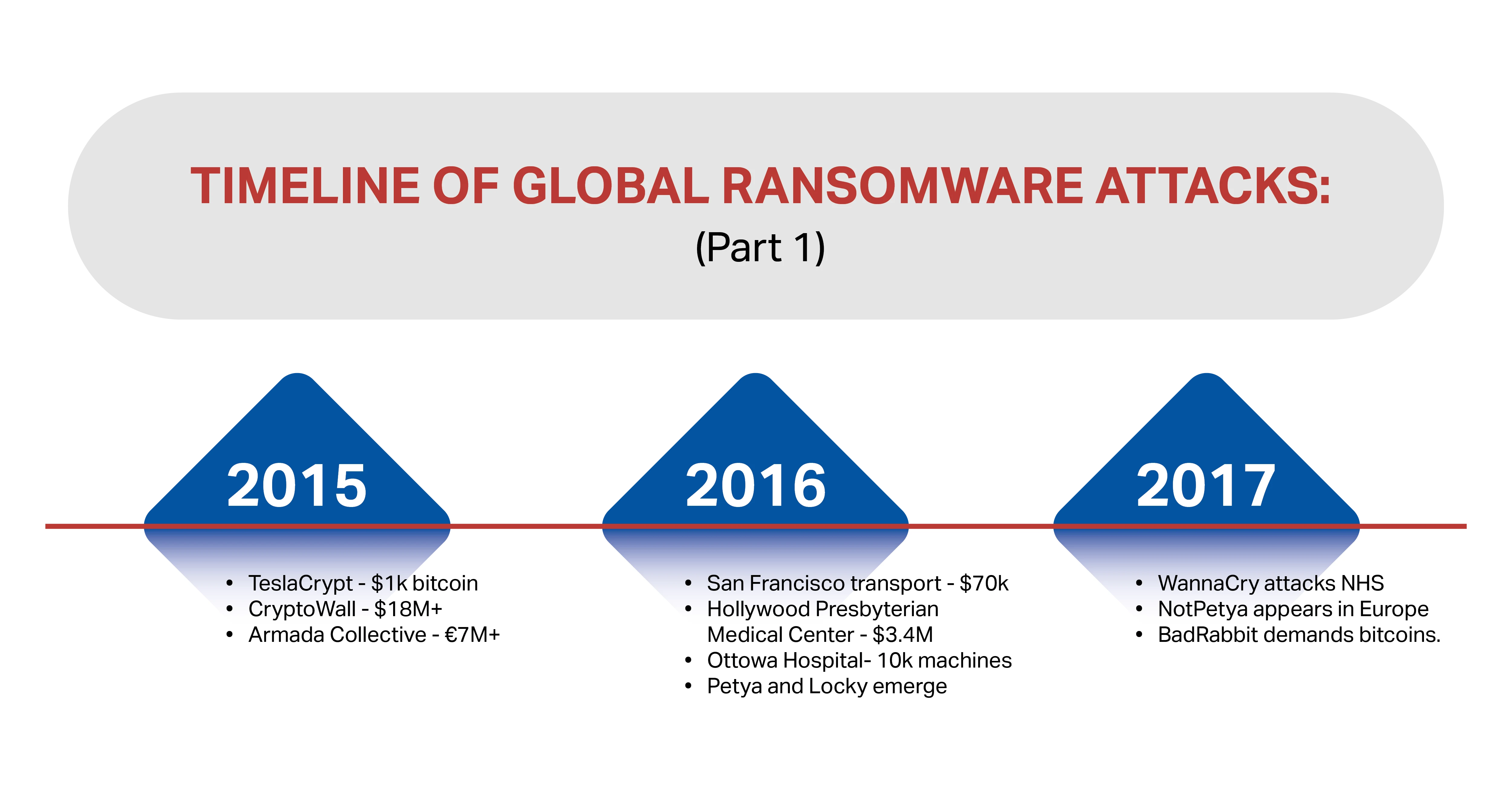
In 2015:
- TeslaCrypt, based on CryptoLocker, targeted gamers and charged a ransom of up to $1k in bitcoin to release infected systems.
- CryptoWall – one of the most common ransomware types managed to earn more than $18 million by the middle of the year and resulted in an FBI advisory.
- Armada Collective targeted Greek financial institutions and demanded more than seven million Euros in ransom. It was the warning shot that saw banks rapidly run towards robust security.
In 2016:
- The San Francisco transport system was hit by ransomware that gave many people free rides, but didn’t impact on the overall transport system. However, it did result in a ransom demand of $70,000
- The Hollywood Presbyterian Medical Center was held to ransom for $3.4 million. This attack was significantly more successful as it prevented anyone from accessing critical patient data, networks and computers for ten days.
- Ottowa Hospital lost nearly 10k machines to ransomware but managed to recover the data thanks to its investment into robust backup and recovery processes.
- Kentucky Methodist Hospital, Chino Valley Medical Center and Desert Valley Hospital were also attacked.
- Petya arrived on the scene – this advanced ransomware was one of the first sold as ransomware-as-a-service.
- Locky arrived and was labelled the most commonly used and the most virulent ransomware.
In 2017:
- WannaCry made most companies cry whenever it was successful. Perhaps its most high profile success story was its attack on the NHS.
- NotPetya appeared in Europe and earned its name because it used some of the Petya code but wasn’t quite the same ransomware problem.
- BadRabbit was identified by Kaspersky – it used a drive-by attack to penetrate hundreds of systems and demanded bitcoins as ransom.
So far, it’s clear that if ransomware can be a service, then protection can be too, and as-a-service protection means backup, restore, data protection and security wrapped into a bundle that delivers, among other things, peace of mind. In Part 02 we look at what happened from 2018 to 2022, and at some of the alarming attacks that have already taken place in 2023 and at how important protection has become for companies all over the world.
Discover how Strategix delivers data protection as a service with Rubrik.